In this week's Security Advisory:
- Security Advisory Update: Zero-Day (CVE-2023-20198) in Cisco IOS XE Software Web UI
- Critical Remote Code Execution Vulnerabilities (CVE-2023-35182, CVE-2023-35185, and CVE-2023-35187) in SolarWinds Access Rights Manager
- Vulnerabilities (CVE-2023-34048 and CVE-2023-34056) in VMware vCenter Server Could Lead to Remote Code Execution
- Okta Discloses Breach in its Support Case Management System
- Security Updates Released for Google Chrome and Mozilla Products
Cisco no longer believes that attackers were leveraging an older, patched vulnerability (CVE-2021-1435) in attacks against IOS XE devices. Cisco now believes that there was a second zero-day, now being tracked as CVE-2023-20273, that was leveraged along with CVE-2023-20198 to deploy malicious code on vulnerable systems. CVE-2023-20273 is a vulnerability in the web UI feature that allows an attacker to elevate the privileges of a local user to root and execute malicious code on the vulnerable system. CVE-2023-20273 received a CVSS score of 7.2 out of a possible 10. It is important to note that while a new zero-day was identified in this attack, Cisco still recommends applying the latest patch to all affected systems.
Many of the versions affected by this attack are scheduled to receive an update within the next couple of days. Those updates should be applied as soon as they become available. Below is an updated patch schedule released by Cisco:
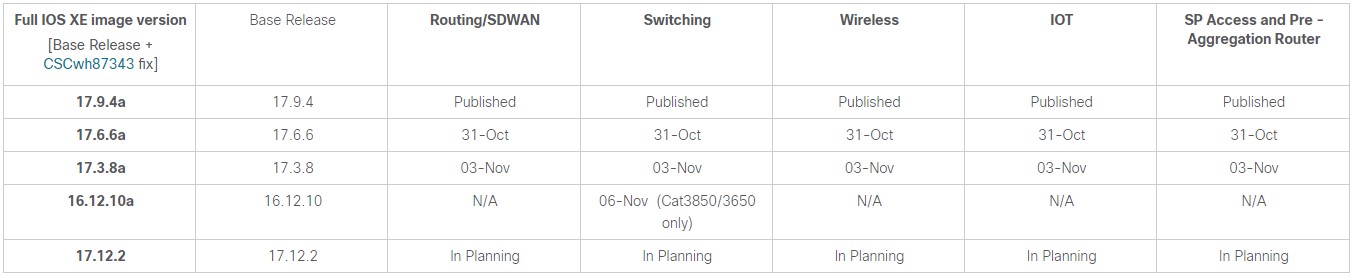
https://www.securityweek.com/cisco-finds-second-zero-day-as-number-of-hacked-devices-drops/
Updated Security Advisory - October 23rd, 2023
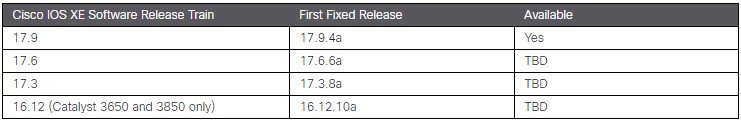
Cisco released the first software update to fix a critical vulnerability (CVE-2023-20198) in Cisco IOS XE devices on Sunday, October 22, 2023. Cisco plans to roll out more updates for other affected versions shortly. Organizations are strongly encouraged to apply those patches as soon as they become available. To stay up to date with the latest patches, navigate to the following link: https://www.cisco.com/c/en/us/support/docs/ios-nx-os-software/ios-xe-dublin-17121/221128-software-fix-availability-for-cisco-ios.html
The following fixed versions are currently available:
Updated Security Advisory - October 20th, 2023
Cybersafe is continuing to monitor developments regarding the critical vulnerability (CVE-2023-20198) in Cisco IOS XE devices. New information reveals that Cisco plans to release an official fix for this vulnerability on Sunday, October 22, 2023. The patch will be available to download from the Cisco Software Download Center. Cybersafe will continue to disseminate updated information as it becomes available and as is deemed pertinent and actionable.
Updated Security Advisory - October 18th, 2023
New information suggests that attackers have infected over 10,000 Cisco IOS XE devices with malicious code. Threat actors are not only exploiting CVE-2023-20198 to create local user accounts but are leveraging an older, patched vulnerability (CVE-2021-1435) to assist in infecting target hosts. This implanted code allows an attacker to execute arbitrary code on affected systems.
While no patch or workaround has been released for CVE-2023-20198, organizations should strongly consider disabling the HTTP server feature on internet-facing systems, or at a minimum restricting it to a trusted set of known authorized IP addresses.
Original Security Advisory - October 16th, 2023
Cisco disclosed a zero-day in the web User Interface (Web UI) feature of IOS XE Software that is being actively exploited in the wild. The zero-day, CVE-2023-20198, allows a remote, unauthenticated attacker to create a highly privileged account on the device, effectively granting the unauthorized user full control of the affected system. Cisco has given the zero-day a CVSS score of 10 out of 10, the highest score a vulnerability can receive.
This zero-day affects Cisco IOS XE Software if the web UI feature is enabled.
Cisco has not released a patch for this zero-day. However, they recommend that customers disable the HTTP server feature on internet-facing systems until a patch becomes available. Navigate to the following link for instructions on how to disable this feature: https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
- https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
- https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/
- https://www.bleepingcomputer.com/news/security/cisco-warns-of-new-ios-xe-zero-day-actively-exploited-in-attacks/
- https://nvd.nist.gov/vuln/detail/CVE-2023-20198
- https://www.bleepingcomputer.com/news/security/over-10-000-cisco-devices-hacked-in-ios-xe-zero-day-attacks/
- https://www.cisco.com/c/en/us/support/docs/ios-nx-os-software/ios-xe-dublin-17121/221128-software-fix-availability-for-cisco-ios.html
- https://www.securityweek.com/cisco-finds-second-zero-day-as-number-of-hacked-devices-drops/
Critical Remote Code Execution Vulnerabilities (CVE-2023-35182, CVE-2023-35185, CVE-2023-35187) in SolarWinds Access Rights Manager
Eight (8) vulnerabilities were found in SolarWinds Access Rights Manager, of which three (3) were deemed critical and could lead to remote code execution. The three vulnerabilities are CVE-2023-35182, CVE-2023-35185, and CVE-2023-35187. CVE-2023-35182 is due to an improper input validation within the createGlobalServerChannelInternal method. CVE-2023-35185 is due to an improper input validation within the OpenFile method. CVE-2023-35187 is due to an improper input validation within the OpenClientUpdateFile method. If the vulnerabilities are successfully exploited, a remote, unauthenticated attacker could execute code with SYSTEM-level privileges.
The following versions are affected:
- SolarWinds Access Rights Manager version 2023.2
- https://documentation.solarwinds.com/en/success_center/arm/content/release_notes/arm_2023-2-1_release_notes.htm
- https://www.darkreading.com/vulnerabilities-threats/critical-solarwinds-rce-bugs-enable-unauthorized-network-takeover
- https://www.securityweek.com/solarwinds-patches-high-severity-flaws-in-access-rights-manager/
- https://www.zerodayinitiative.com/advisories/ZDI-23-1564/
- https://www.zerodayinitiative.com/advisories/ZDI-23-1565/
- https://www.zerodayinitiative.com/advisories/ZDI-23-1567/
Vulnerabilities (CVE-2023-34048 and CVE-2023-34056) in VMware vCenter Server Could Lead to Remote Code Execution
VMware released updates to address two (2) vulnerabilities in its vCenter Server that could lead to remote code execution. The first vulnerability, CVE-2023-34048, is an out-of-bounds write weakness in vCenter's DCE/RPC protocol implementation and could allow a remote, unauthenticated attacker with network access to execute remote code on the vulnerable server. CVE-2023-34048 has received a CVSS score of 9.8 out of a possible 10. The second vulnerability, CVE-2023-34056, is a partial information disclosure vulnerability that could allow an attacker with non-administrative privileges to the vulnerable server to gain access to unauthorized data. CVE-2023-3405 received a CVSS score of 4.3 out of a possible 10.
The following versions are affected:
- VMware vCenter Server prior to version 8.0 (8.0U1d or 8.0U2)
- VMware vCenter Server prior to version 7.0 (7.0U3o)
- VMware Cloud Foundation prior to versions 5.x and 4.x
More Reading/Information
- https://www.vmware.com/security/advisories/VMSA-2023-0023.html
- https://www.bleepingcomputer.com/news/security/vmware-fixes-critical-code-execution-flaw-in-vcenter-server/
- https://www.helpnetsecurity.com/2023/10/25/cve-2023-34048/
Okta Discloses Breach in its Support Case Management System
Okta recently disclosed a breach in its support case management system. Threat actors used stolen credentials to access Okta's support case management system and viewed HTTP Archive (HAR) files containing customer session tokens and cookies. HAR files can track all the logging of a web browser's interaction with a site and often contain sensitive information like session tokens or cookies. If stolen, an attacker could use this information to impersonate valid users. This breach only impacts the support case management system. It does not affect the production Okta service or the Auth0/CIC case management system.
To mitigate this attack, Okta has revoked embedded session tokens and is encouraging customers to sanitize credentials within HAR files before sharing them to the support case management system.
Okta states, "All customers who were impacted by this have been notified. If you're an Okta customer and you have not been contacted with another message or method, there is no impact to your Okta environment or your support tickets."
More Reading / Information
- https://sec.okta.com/harfiles
- https://www.beyondtrust.com/blog/entry/okta-support-unit-breach
- https://krebsonsecurity.com/2023/10/hackers-stole-access-tokens-from-oktas-support-unit/
- https://www.bleepingcomputer.com/news/security/okta-says-its-support-system-was-breached-using-stolen-credentials/
Security Updates Released for Google Chrome and Mozilla Products
There were security updates released for Google Chrome and Mozilla products. The most severe could lead to arbitrary code execution.
Google Chrome addressed two (2) vulnerabilities, with one (1) given a severity rating of "High". These vulnerabilities affect Windows, Mac, and Linux.
Mozilla addressed twenty-eight (28) vulnerabilities, with eight (8) given a severity rating of "High". These vulnerabilities affect Firefox for iOS, Thunderbird, Firefox ESR, and Firefox.
More Reading / Information
- https://chromereleases.googleblog.com/2023/10/stable-channel-update-for-desktop_24.html
- https://www.mozilla.org/en-US/security/advisories/
Recommendations
Please review your environment to ensure the above-mentioned issues are patched in a timely manner. It is security best practice to regularly update and/or patch software to the latest versions. The vulnerabilities above highlight the security benefits of limiting deployed software to "vendor-supported versions" only. This dramatically increases the likelihood that new vulnerabilities have a patch issued for them. Likewise, Cybersafe strongly encourages maintaining an inventory of current software in your environment, which helps ensure and inform your patch and vulnerability management program.



